A Guide to GPS Spoofing Visibility in OSINT Tools
By Samantha Bamberger

GPS spoofing has moved away from an expensive tactic used by militaries to an affordable option, and open-source intelligence (OSINT) analysts are seeing the impacts more regularly. The uptick in media coverage on spoofing, such as by Forbes and Reuters shows the impacts increasingly affect daily, civilian life. While trash balloons captured the curiosity of many, the same article touches on the increasing concern that GPS spoofing flight locations puts civilians at risk of entering North Korean air space. A viral report by OPSGROUP indicated a 400% increase in GPS spoofing affecting commercial flights in 2024.
What is GPS?
GPS is the abbreviation for the Global Positioning System which is part of the Global Navigation Satellite System (GNSS). In addition to tracking geospatial positions, the system also tracks dates and times. This array of satellites keeps our devices, from aircraft to your smartwatch, in sync with time and space.
The satellites transmit a continuous radio signal containing the time and a satellite code from a geosynchronous orbit, meaning their coordinates are known and unchanging. Devices receiving the GNSS signal require at least three codes to triangulate their location.
GPS tracking apps can help visualize which satellites are used to calculate the receiver’s location in real time.
What is GPS spoofing?
GPS spoofing occurs when a strong earth-based radio transmitter overrides the satellite signal with a fake one. The receiving device then incorrectly calculates its location and may receive fake time signatures as well.
What is the risk of GPS spoofing?
The risk to commercial aviation is significant, since GPS spoofing could cause a jet to veer off course into protected airspace, where it could be perceived as hostile. Any vehicle that relies on GPS signals for navigation — from autonomous cars to rideshares to delivery trucks — could be affected by receiving incorrect location data.
Criminals can use GPS spoofing to misdirect trucks to steal cargo, or to hide stolen vehicles by sending false signals to the onboard GPS receiver. Some apps make it possible for any user to spoof their GPS location, for example, to appear as if they are another city while using a dating app. More seriously, GPS signal tampering could affect emergency services, leading to ambulances being sent astray.
Detect GPS spoofing using OSINT tools
Because it has become more prevalent, OSINT professionals are more likely to detect GPS spoofing during data analysis. While innocuous uses (such as for online dating) may not affect the results, they will be noticeable and increase the need for careful filtering and examination of data points.
As an example, the tracks in the image below look like regular flights above international waters. However, when searching for a longer period a clearer picture emerges. These “flights” date back to 2021 and included trips from pole to pole in two hours. Looking at these orbiting tracks, it was obvious they weren’t flights.
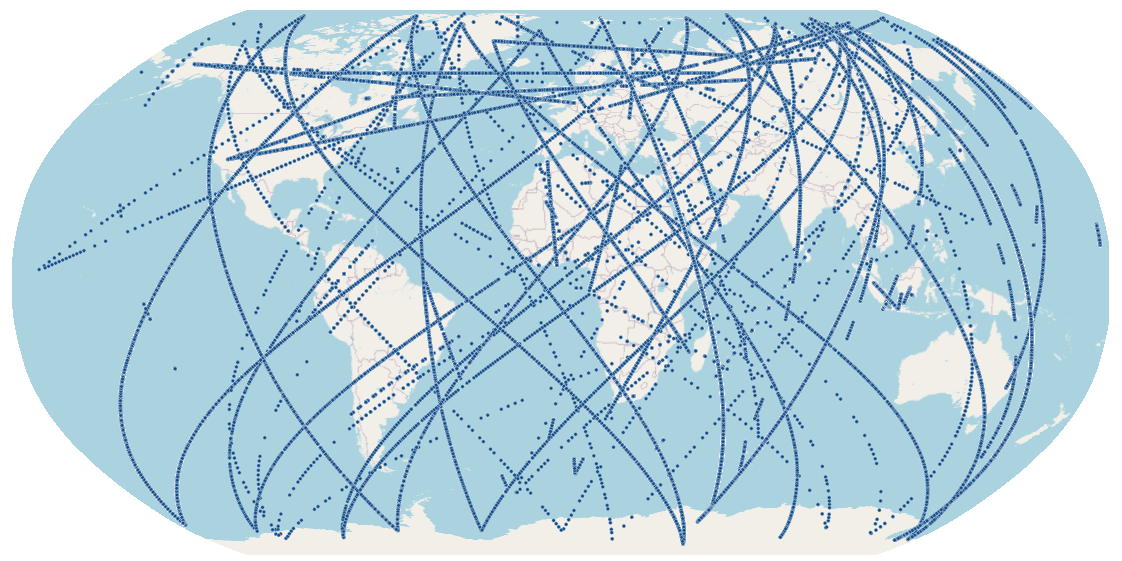
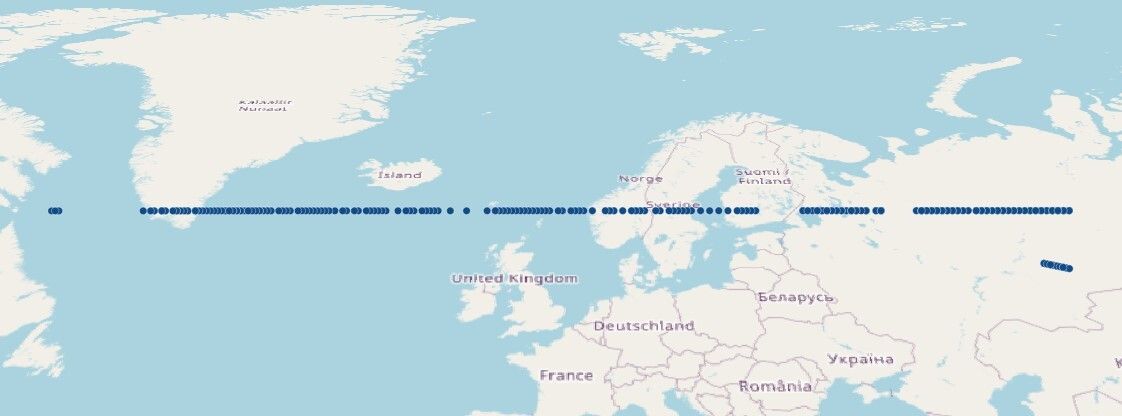
Narrowing the picture a little, I checked the first ten minutes of activity I could find. That resulted in 243 pings within ten minutes spanning over 5,500 km (3,400 mi). I reasonably assumed the receiver was not traveling 5,500 km in the straightest line possible across the northern hemisphere and determined GPS spoofing had polluted my dataset. I found two other occurrences and clearly indicated them so other analysts would ignore them.
Suggestions
Here are some suggestions for dealing with GPS data that may be in error due to spoofing:
- Have ways to clear the clutter — remove the spoofs from your results when possible, or leave notes so others know to ignore the noise
- Be open to the possibility of GPS spoofing impacting your dataset. This can affect cell phones, vessels, aircraft, cars, and more
- Spoofing has been occurring for longer than recent media coverage so just because you’re looking at a 2- or 3-year-old dataset doesn’t mean it won’t be impacted
- Search the proximity of the initial finding to see if other GPS-dependent devices are affected
End Notes
Princeton’s Alain Kornhauser- https://www.princeton.edu/~alaink/Orf467F07/GNSS.pdf
Kaspersky - https://www.kaspersky.com/blog/gps-spoofing-protection/26837/
Aviation Week - https://aviationweek.com/business-aviation/safety-ops-regulation/serious-threat-gps-spoofing-analysis
Nord VPN - https://nordvpn.com/blog/gps-spoofing/
Springer Link - https://link.springer.com/article/10.1007/s10291-024-01719-2
Disclaimer
All names, companies, and incidents portrayed in this document are fictitious. No identification with actual persons (living or deceased), places, companies, and products are intended or should be inferred.